T4K3.news
Windows RPC EPM vulnerability patch released
Microsoft patched CVE-2025-49760 in July 2025, but many networks still face exposure if patches lag or if RpcEpRegister is misused
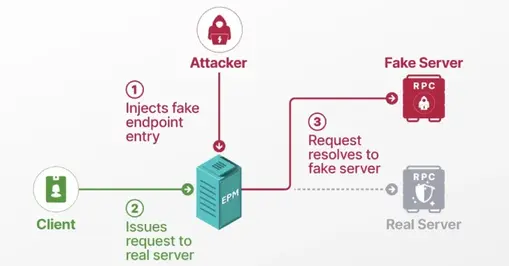
Researchers describe a patched Windows RPC flaw that can enable spoofing, hash theft and privilege escalation.
Windows RPC poisoning opens path to domain privilege escalation
Researchers have outlined how a patched Windows Remote Procedure Call (RPC) flaw could be abused to spoof a built in server and impersonate trusted services. Tracked as CVE-2025-49760, the vulnerability was fixed in July 2025 as part of Microsoft’s Patch Tuesday updates. Microsoft labels it a Windows Storage spoofing bug that affects the Endpoint Mapper, which maps an RPC client to a server endpoint. By manipulating how an interface is registered, an attacker can perform an EPM poisoning attack that lets an unprivileged user pose as a legitimate service and cause a protected process to authenticate to a server chosen by the attacker.
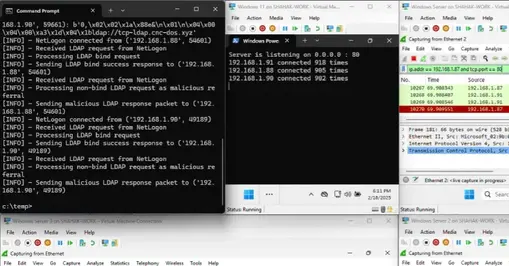
In practical terms, the attack chain begins with a scheduled task that runs on user login, followed by registering the Storage Service interface. The attacker then forces the Delivery Optimization service to contact the attacker’s dynamic endpoint and, in turn, prompts the service to receive an SMB share from a rogue server. This exchange can leak the machine account NTLM hash, enabling an ESC8 privilege escalation path toward domain controllers via tools like Certipy. SafeBreach also released RPC-Racer to flag insecure RPC services and warns that the EPM could be extended to adversary in the middle and denial of service scenarios by registering multiple interfaces. Security teams are urged to monitor RpcEpRegister calls and enable ETW tracing to detect suspicious mappings.
The finding has rekindled a broader discussion about how much the Windows security model relies on trust in internal components. It also highlights the gap between patch release and practical protection in large organizations that run mixed environments and delayed-start services that may leave interfaces unregistered at boot.
Key Takeaways
"External control of file name or path in Windows Storage allows an authorized attacker to perform spoofing over a network."
Microsoft advisory on CVE-2025-49760 describing the flaw
"I was shocked to discover that nothing stopped me from registering known, built-in interfaces that belong to core services."
Ron Ben Yizhak on findings at DEF CON 33
"There were no security checks completed by the EPM."
Ben Yizhak on EPM behavior during testing
"The identity of an RPC server should be checked before trust is granted."
Researcher call for stronger RPC verification
The episode shows a real risk in core OS components that assume trust inside a corporate network. When identity checks for RPC servers are weak, attackers can rewrite how endpoints are discovered and connected, turning trusted processes into unwitting pawns. The emphasis on defense in depth matters now more than ever, particularly as enterprises juggle patch fatigue and complex service dependencies. The case also underscores why tools that reveal misregistrations and unusual RPC activity should become standard, not optional.
Beyond the technical details, the incident raises questions about patch cadence, asset inventory and the need for zero trust thinking inside data centers. It is a reminder that even well defended systems can rely on fragile routines such as delayed starts, which create blind spots that attackers can exploit. The bottom line is simple: better visibility and stronger identity checks for internal services are no longer optional.
Highlights
- Trust in the endpoint mapper must be earned not assumed
- If a service boots late, an attacker can register its interface first
- The identity of an RPC server should be checked
- Patches arrive late for many networks
Risk from EPM poisoning on unpatched systems
The patched flaw still poses real risk for networks that have not applied the fix or that rely on delayed service starts and misregistered interfaces. Attack chains can lead to local and domain privilege escalation and step up to credential theft, stressing the need for rapid patching and stronger internal checks.
Patching fixes the vulnerability, but resilience depends on how quickly organizations translate fixes into stronger internal controls.
Enjoyed this? Let your friends know!
Related News
Win-DDoS Flaws Threaten Domain Controllers
WinRAR patch release

Emergency Patch Released for SharePoint Attack
Microsoft Issues Urgent Patch for SharePoint Vulnerability

Unpatched Exchange servers risk domain compromise

Microsoft issues emergency patch for SharePoint vulnerabilities

Trend Micro warns of critical Apex One vulnerability

Microsoft warns of serious flaw in Exchange Server
