T4K3.news
Win-DDoS Flaws Threaten Domain Controllers
Four Windows LDAP RPC flaws could turn public domain controllers into a DDoS botnet; patches were released in 2025.
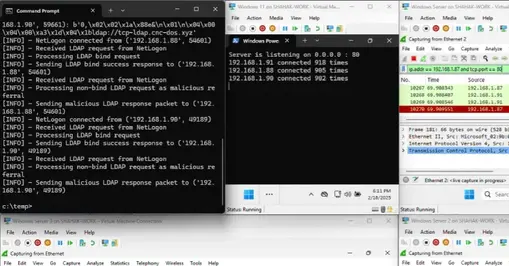
Security researchers warn of four Windows flaws that abuse RPC and LDAP to convert public domain controllers into a stealth DDoS botnet, with patches released in 2025.
Win-DDoS Flaws Turn Public Domain Controllers Into DDoS Botnet
Researchers from SafeBreach describe Win-DDoS as a new technique that exploits LDAP and CLDAP referral flows to coax domain controllers into contacting an attacker controlled server. The DCs then forward LDAP queries to the attacker server and follow a list of referrals that directs traffic to a single IP and port, creating a coordinated source of traffic. The method does not require code execution or stolen credentials, making it easier for attackers to trigger a large scale effect.
Microsoft fixed the flaws in 2025, addressing several CVEs tied to LDAP LSASS Netlogon and Print Spooler. The researchers warn that these flaws can crash controllers or force reboots when attackers feed long referral lists, and that the attack can be carried out against systems exposed on the internet. The findings challenge the idea that DoS risks are limited to public services and show how internal infrastructure can be misused to harm business operations.
Key Takeaways
"Internal trust can become a weapon when referrals are unchecked."
Editorial note on internal risk
"Zero-click flaws rewrite how we model DoS risk."
Analyst perspective on threat modeling
"Defense now needs to audit LDAP referrals and segment DCs."
Security expert comment
"Patches exist, deployment across large networks remains a hurdle."
Industry viewpoint
Win-DDoS highlights a shift in threat modeling, where internal services become weapons. It shows that trust within the network can be exploited as easily as trust on the outside. The report urges defenders to watch not just external access points but also how referral flows and heap memory are managed in domain controllers.
The patching race is real. Enterprises must balance rapid updates with stability, while adding monitoring for referral traffic and enforcing tighter segmentation of domain controllers. The attack underscores the need for better visibility into identity services and for designs that limit the ripple effect of a single misconfigured referral.
Highlights
- Internal trust can become a weapon when referrals are unchecked.
- Zero click flaws demand a new look at how we model DoS risk.
- Patching is essential but not enough without tightening referral controls.
- A domain controller can become a tool for a DDoS attack.
Patching is essential, but so is rethinking internal trust and monitoring.
Enjoyed this? Let your friends know!
Related News

Trade deadline approaches for MLB teams
Windows RPC EPM vulnerability patch released

Indian authorities ban 25 books in Kashmir

Ranking all FBS programs for the 2025 season

Israeli Forces Face Allegations of War Crimes

Switch 2 Zelda editions receive significant upgrades

World marks Hiroshima anniversary with renewed nuclear fears

Gaza strategy under fresh scrutiny
